Managed Cloud SIEM
Deep insights for threat, risk and compliance management
Todyl Managed SIEM provides the critical visibility, powerful analytics, and flexible data retention necessary to manage a comprehensive cybersecurity and continuous compliance program.
Enterprise Visibility Without the Complexity
Todyl Managed SIEM collects, analyzes, and retains log data from endpoints, end users, networks, cloud services, and applications-delivering comprehensive visibility into client threat, risk, and compliance postures in a single, intuitive interface.
Advanced threat detection made easy
Perform real-time advanced analytics and anomaly detection with:
- Over 500 pre-built, continuously tuned detection rules
- Machine learning-powered behavioral analysis
- Automated correlation and contextualization of security events
- Expert-defined detection logic for emerging threats
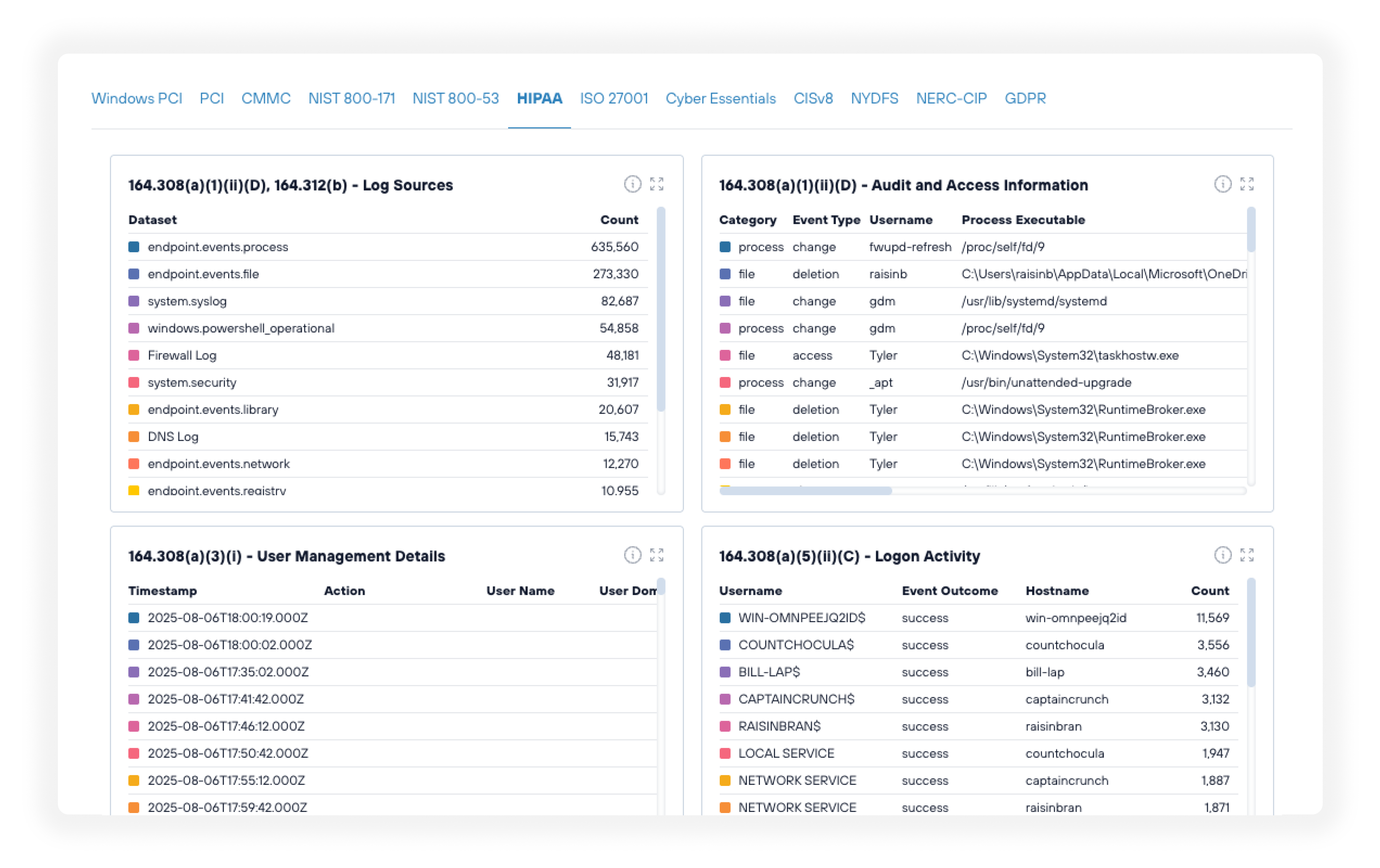
Streamlined compliance and reporting
Make meeting and demonstrating compliance simple with:
- Centralized log management with flexible retention policies
- Customizable reporting templates for regulatory requirements
- Multi-tenant architecture for efficient client management
- Automated compliance tracking and documentation
- Easy-to-generate audit trails and compliance reports
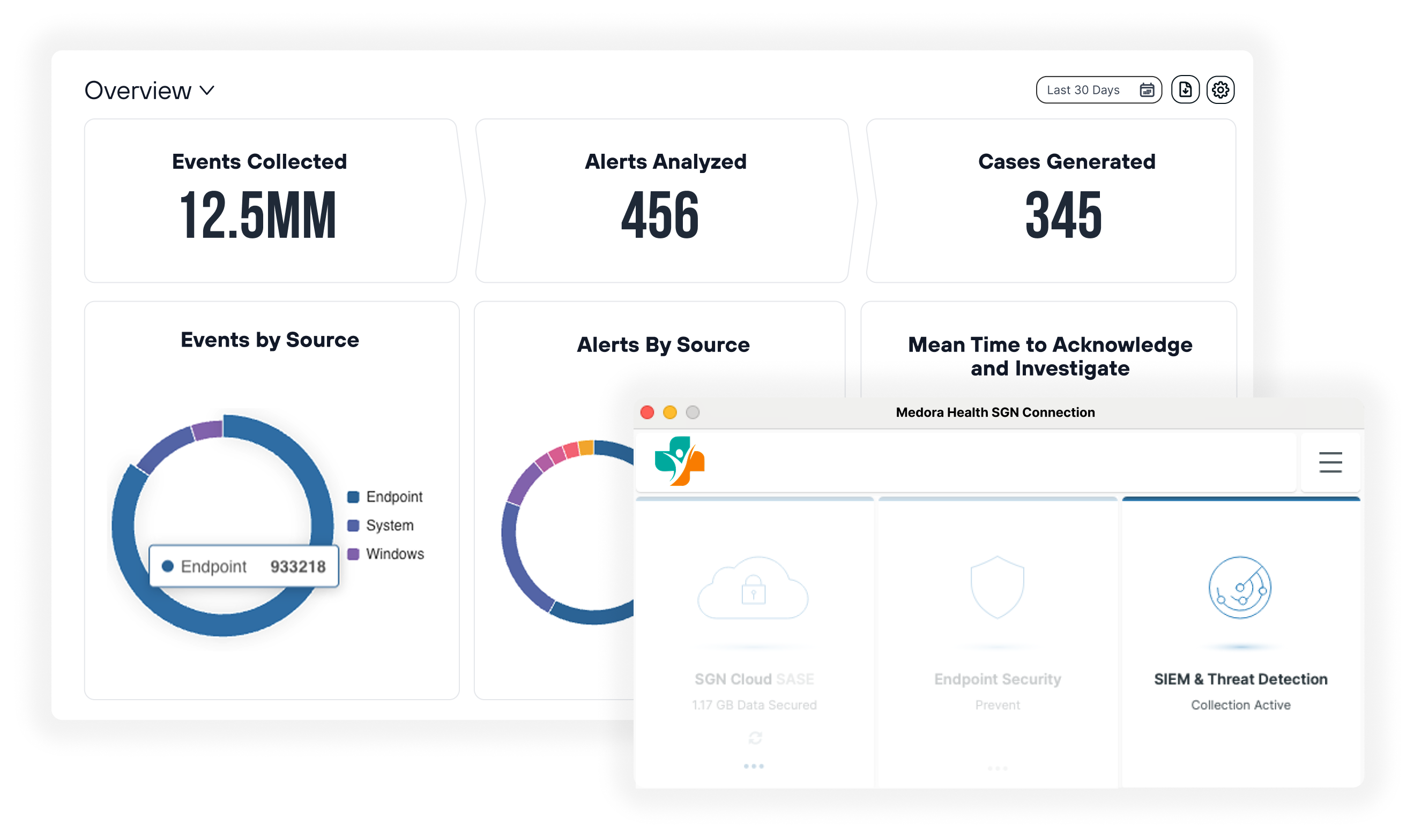
Fast and efficient SOC enablement
Simplify and streamline security operations with:
- Fast deployment with minimal configuration required
- Cloud-native platform scales with your business
- Unified case management streamlines investigations
- Continuous updates and rule refinements from security experts
- Comprehensive training and support included
Why Choose Todyl SIEM?
Deep Visibility, Advanced Detection, and Powerful Reporting
Todyl integrates expert security knowledge with continuously updated detection rules and machine learning to quickly identify critical threats, while powerful forensics accelerate investigation and response times.
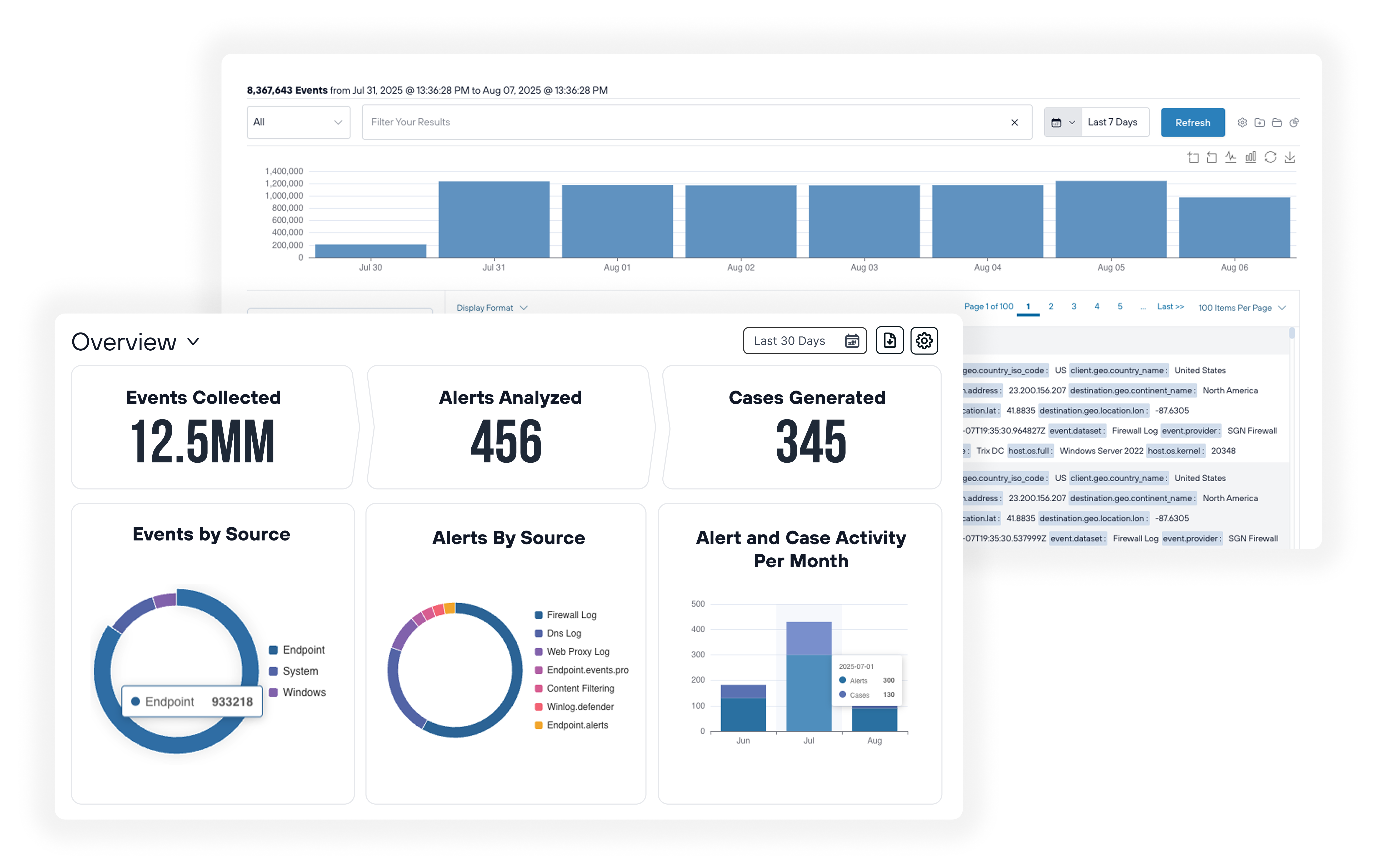
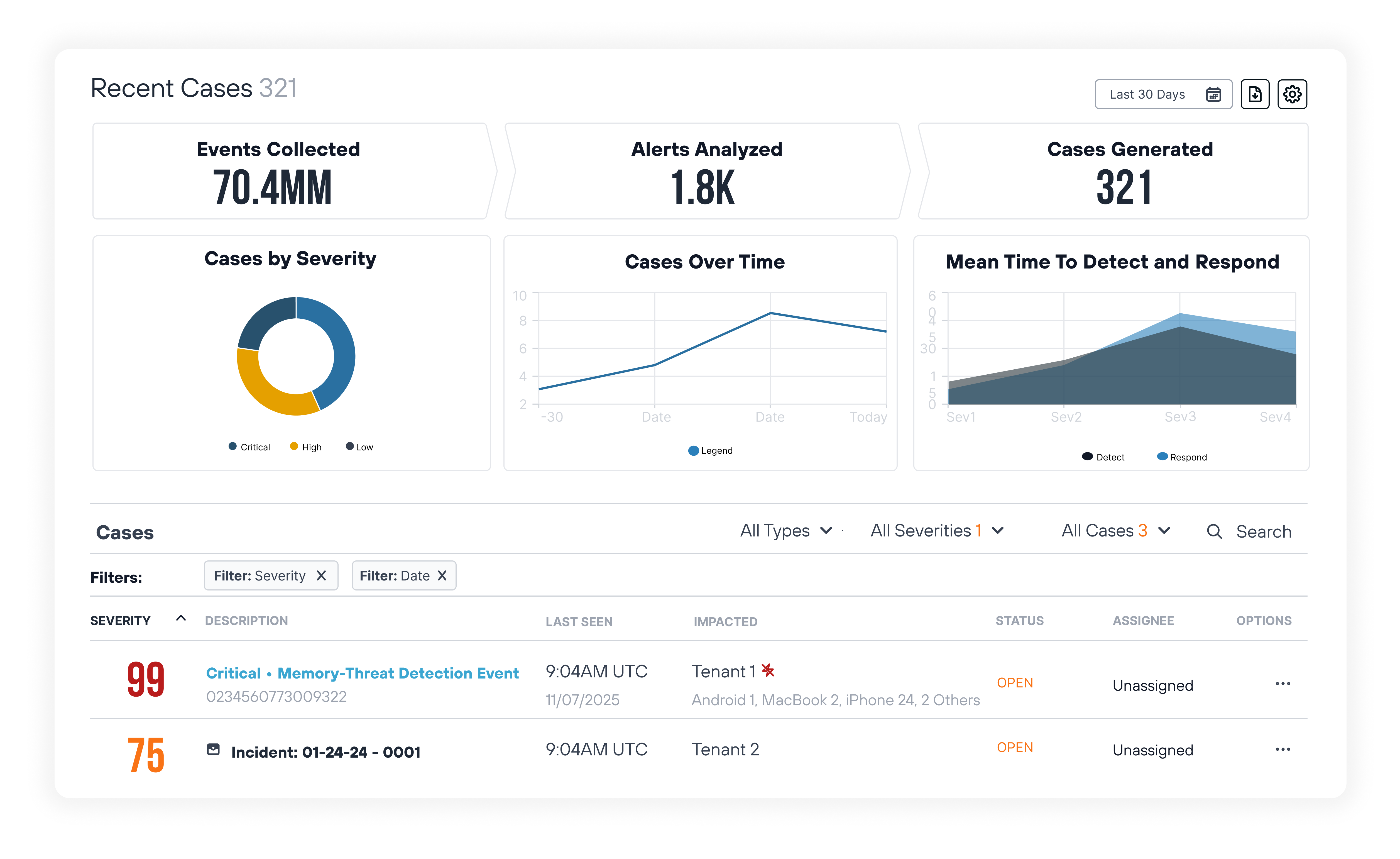
Deep threat visibility
Managed SIEM collects and analyzes log data from a wide range of devices, platforms, and applications to detect and alert on threats for enterprise-class threat management. Out-of-the-box dashboards and reports, and powerful search deliver on-demand visibility.

Intelligent threat detection & response
Todyl’s Anomaly Detection Framework analyzes all log and event data to quickly detect critical and advanced threats. ML-driven analytics identify real threats and automatically consolidate relevant event context to help eliminate false positives and streamline incident response.
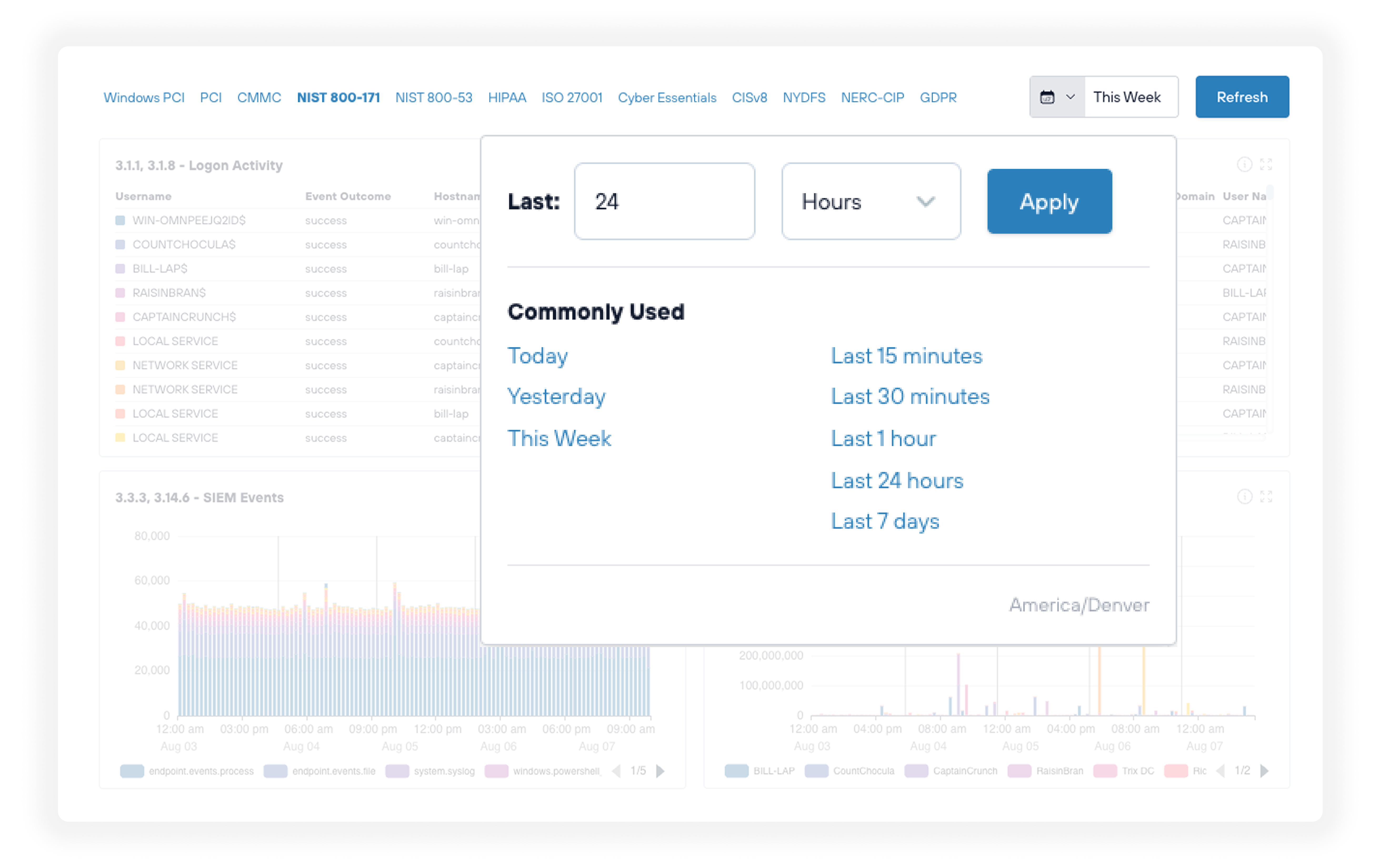
Flexible data management
Collect and aggregate all relevant log data in one location for compliance management and forensic analysis. Easily configured data retention policies can adapt to any compliance requirement while also enabling powerful dashboards and reporting capabilities.
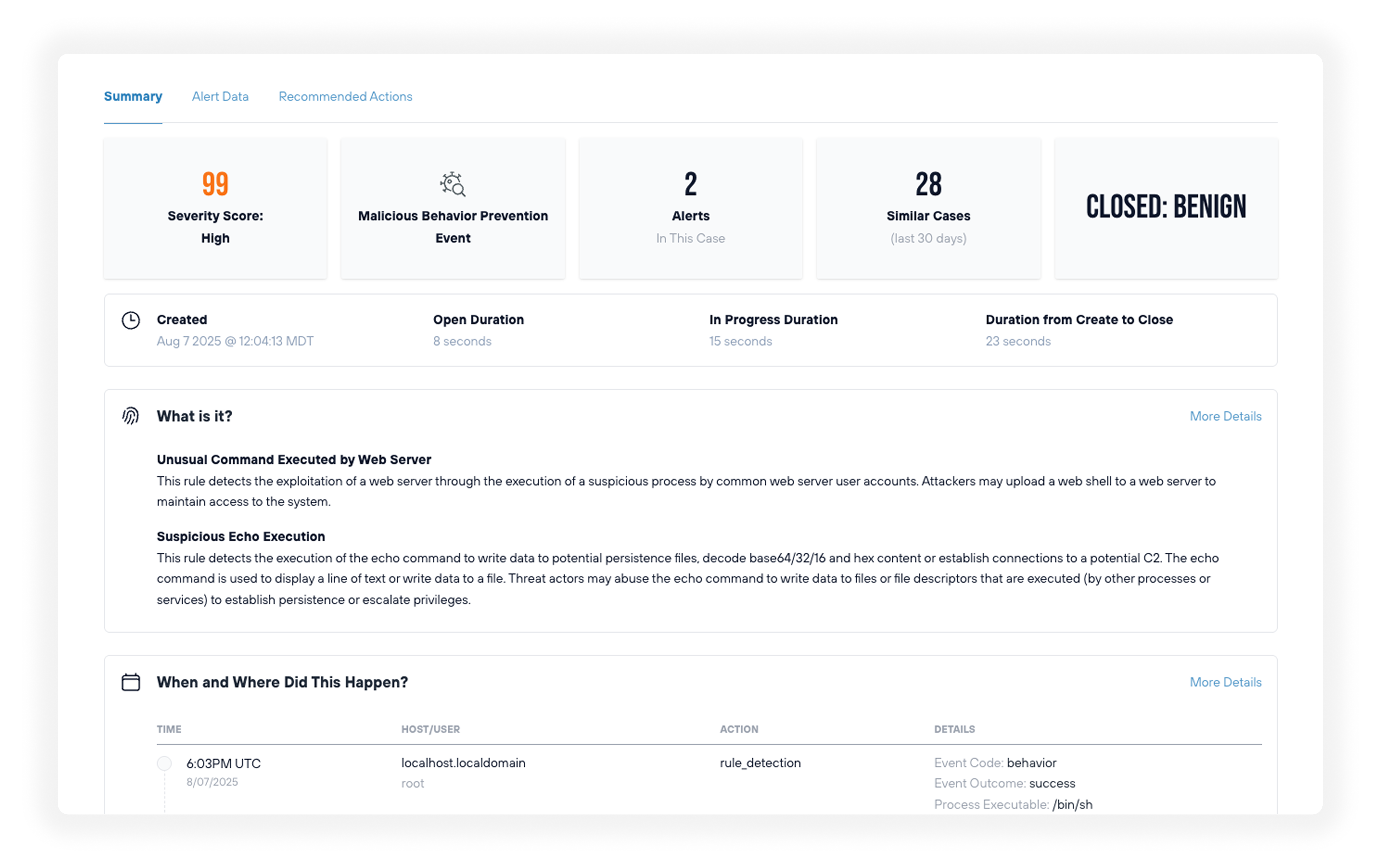
Streamlined incident response
Todyl’s intelligent case management uses powerful machine learning to automatically aggregate alert and event context in a single, easy-to-navigate view. Ech case delivers critical threat insights and remediation assistance to accelerate detection and response times.
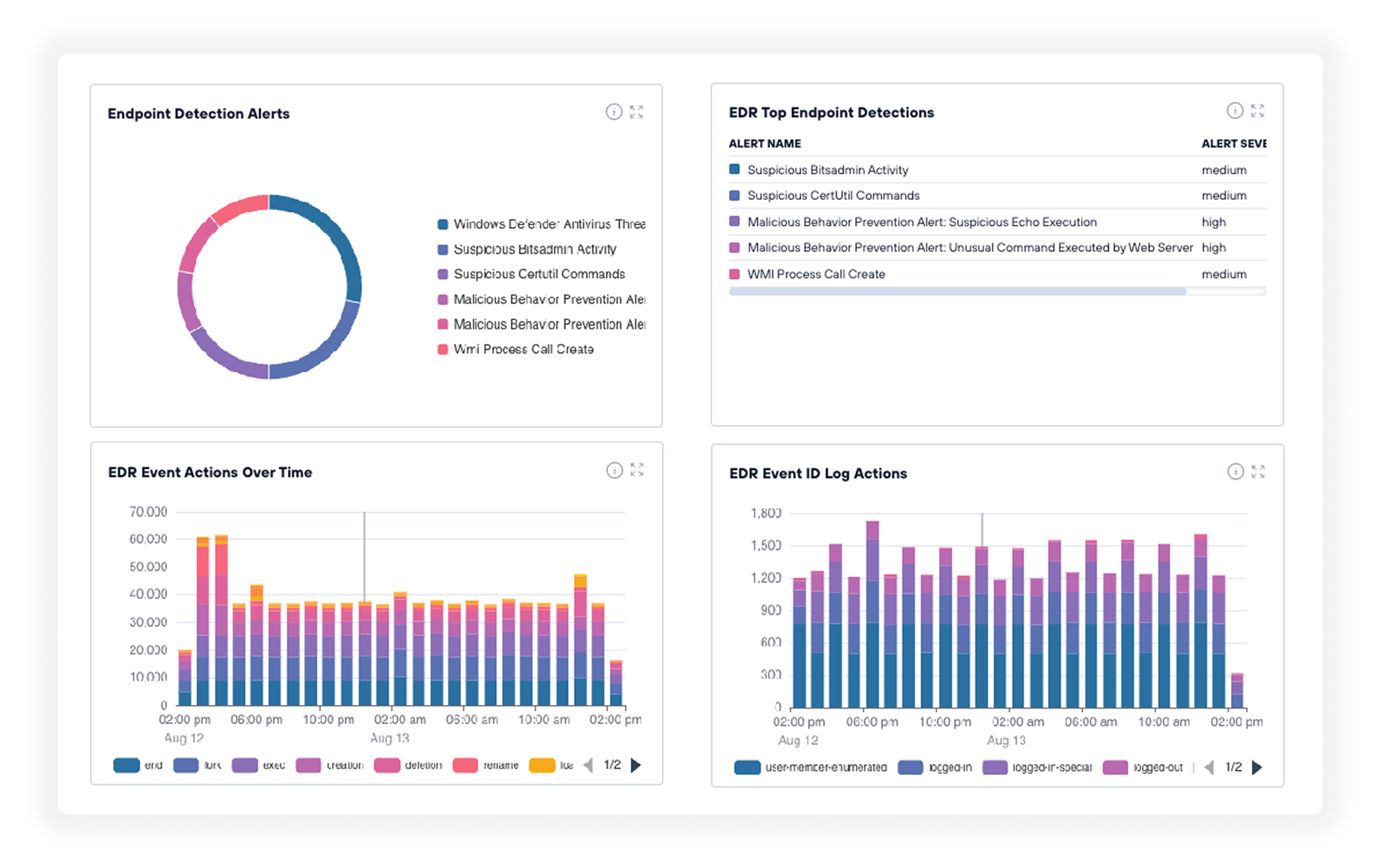
Powerful dashboards & reports
An extensive collection of out-of-the-box and customizable dashboards and reports deliver powerful threat, risk, and compliance management insights for organizations of any size. Macro-level and granular views provide intelligence for delivering effective cybersecurity.
Testimonials
SIEM FAQs
How is Managed Cloud SIEM different from traditional options?
Managed cloud SIEM offloads the hassles that come with traditional SIEMs: hosting, managing, maintaining, and tuning. Instead, Todyl does it for you, giving you concise, contextualized insights into your security events with minimal false positives. That way, you can drill directly into threats that matter without time wasted sifting through logs or hefty upfront costs.
What solutions does SIEM integrate with?
Todyl SIEM natively integrates with dozens of today's top work applications, identity providers, and other security tools. MSP-first, the solution also integrates seamlessly with prominent RMM and PSA solutions to make managing and monitoring multiple client organizations simple. You can also use our prebuilt UDP and TCP syslog collectors to incorporate unique data sources.
Do I need any hardware for SIEM?
No, as a managed cloud solution, SIEM can be used entirely from a single browser window. Unlike traditional SIEMs, you don't need to host it on your own servers to get critical security insights.
How does SIEM improve my cybersecurity program such as detecting insider threats?
SIEM strengthens cybersecurity programs by collecting and analyzing data from across your environment to identify unusual patterns or behaviors. This makes it easier to spot potential insider threats, investigate incidents quickly, and take action before they cause significant damage.
What does SIEM do for compliance?
As a centralized security event repository, SIEM is crucial for many compliance requirements. It provides both ongoing proof of a strong security program and gives by the second insights into how your program operates during security events. It even features premade dashboards for specific compliance frameworks and regulations so you can be audit ready whenever.
How can SIEM help me apply for cyber insurance policies?
SIEM supports cyber insurance applications by centralizing security event data, correlating threats, and generating detailed incident reports. This visibility helps demonstrate strong monitoring practices, rapid detection capabilities, and a proactive security posture, all of which insurers look for when evaluating coverage eligibility.
SIEM Related Content