Identity Threat Detection and Response
Todyl ITDR delivers critical, 24x7 protection from identity-based attacks, privilege abuse, and cloud security threats for organizations of all sizes.
Why ITDR?
Identity-based threats are one of the most dangerous attack vectors for any organization, but small to mid-sized organizations rarely have the resources and expertise to detect and respond to attacks.
Todyl ITDR Delivers
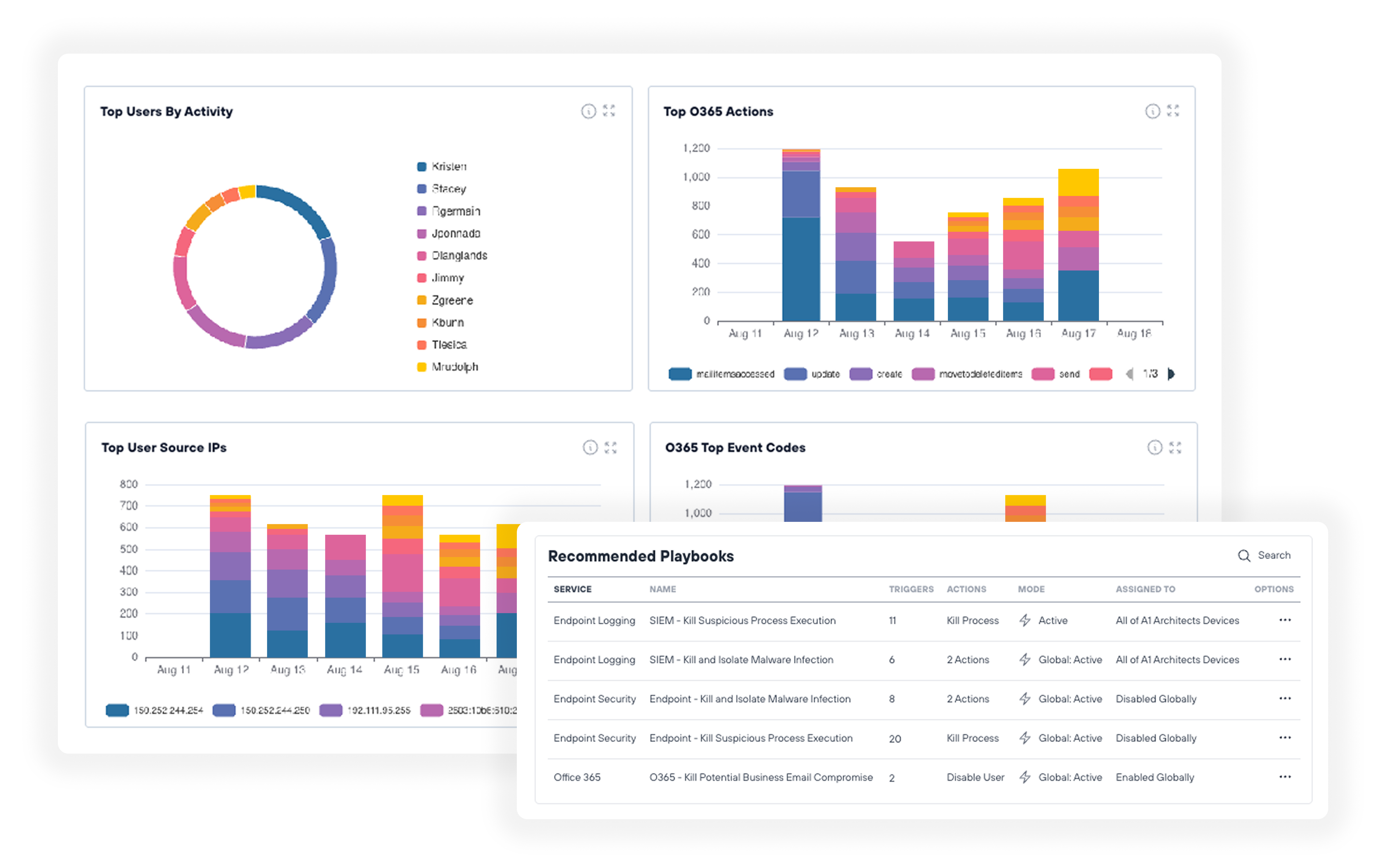
Todyl’s MXDR team delivers 24x7 expert ITDR services for Microsoft 365 and Azure environments, monitoring for anomalous identity usage and account access, at a fraction of the cost of implementing an in-house program.
Continuous monitoring and protection of cloud identities
Rapid containment of advanced attacks (ATOs, AitM, etc.)

Anomalous account access and usage detection
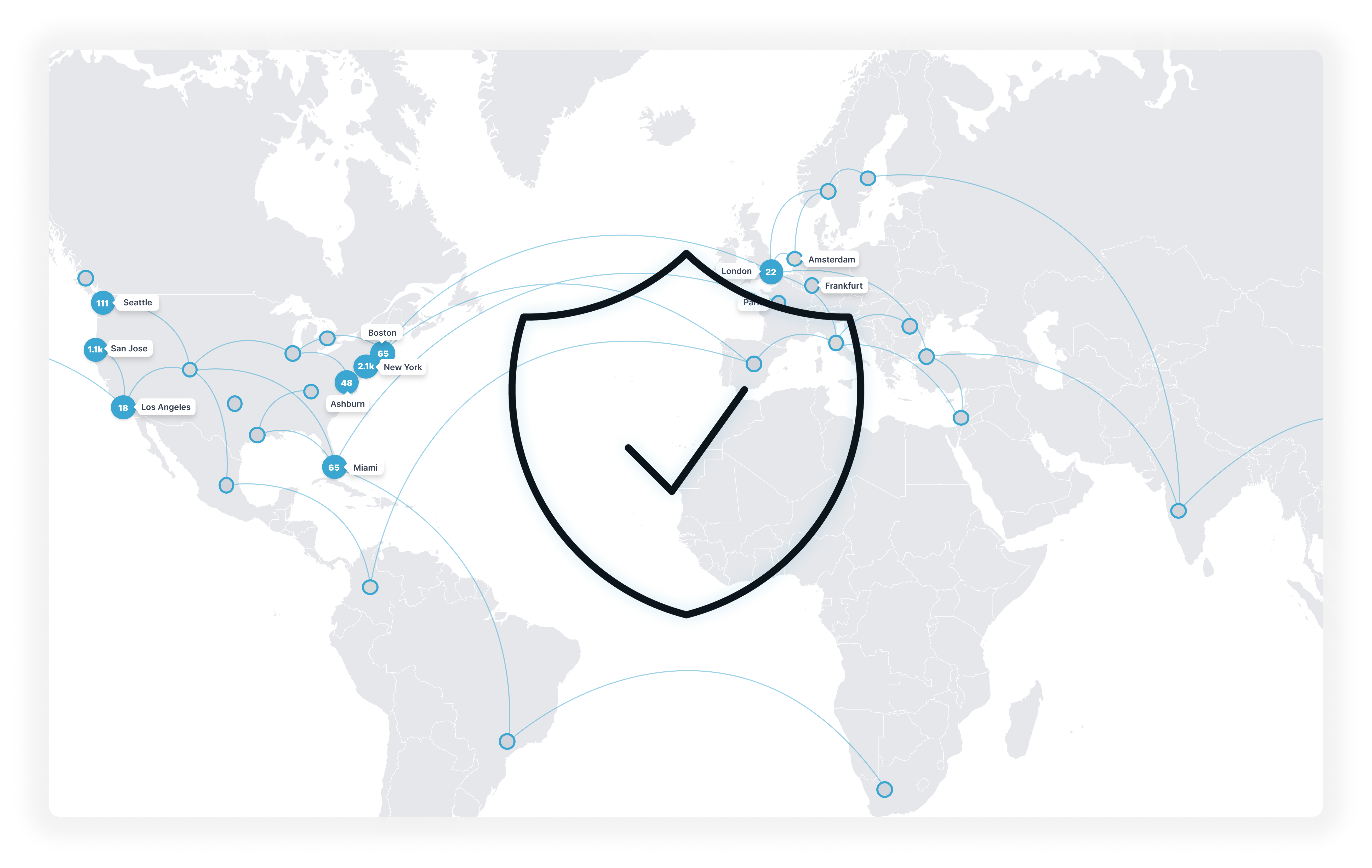
Herd immunity across all Todyl partners (BECs, Ransomware, etc.)
Todyl ITDR in Action
Detecting Business Email Compromises (BECs)
Challenge
BECs lack the IoCs and behavioral markers that trigger alerts in traditional
security tools.
Solution
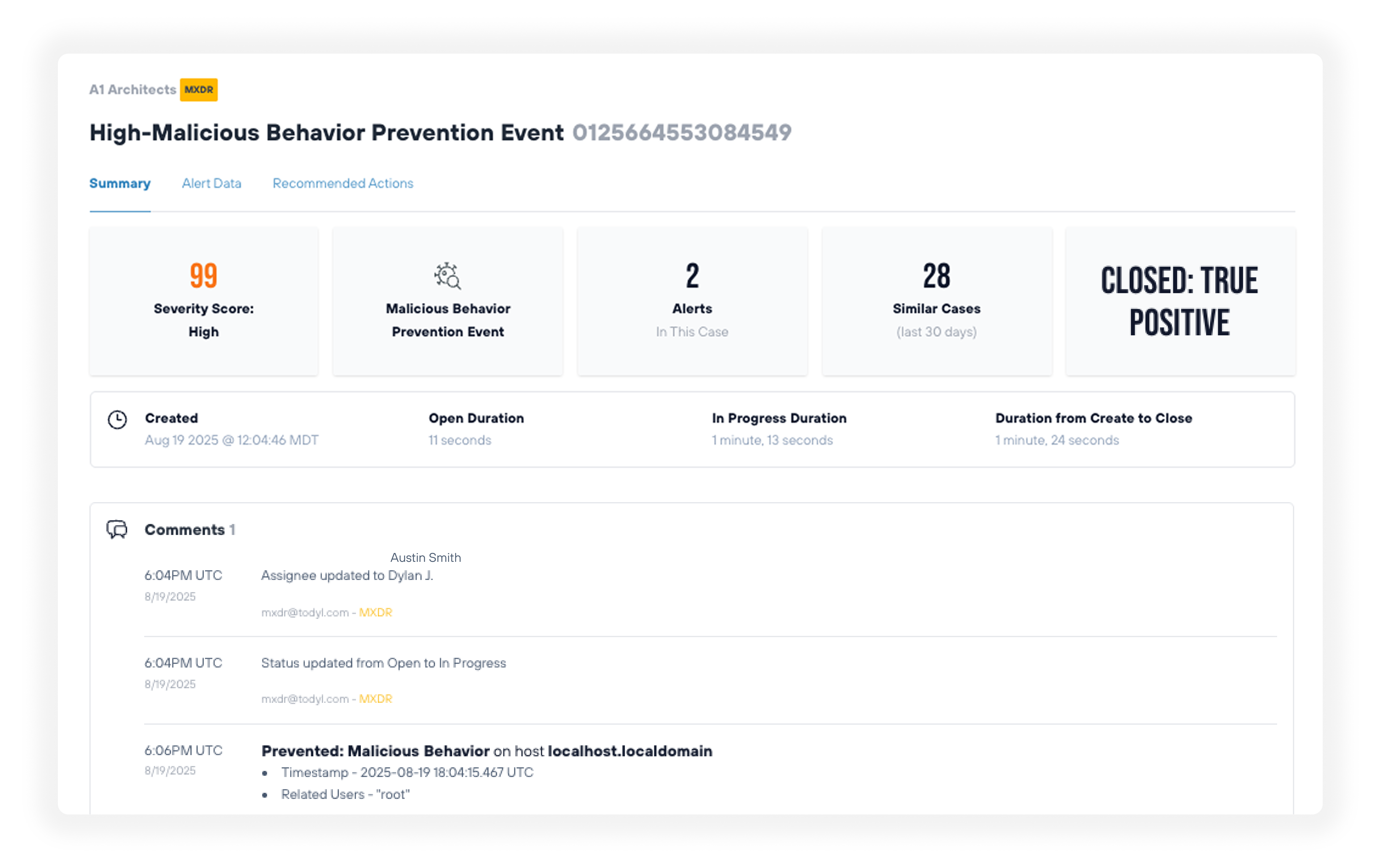
Todyl ITDR analyzes extensive telemetry to detect identity-based attacks quickly.
Benefit
Partners receive proactive notification of BECs with expert analysis and automated containment.
Detecting Insider Threats and Stolen Credentials
Challenge
Credential-based attacks evade detection by mimicking normal user behavior.
Solution
Todyl ITDR analyzes identity-related activity to detect and investigate suspicious activity.
Benefit
SASE and LZT micro segmentation help contain unauthorized access and lateral movement.
Testimonials
Title
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Suspendisse varius enim in eros elementum tristique.
