Cybersecurity Solutions for Manufacturing
Manufacturing organizations need cybersecurity that protects critical operations and valuable intellectual property while maintaining operational efficiency. Our platform handles the complex security expertise, delivered through partners who understand manufacturing operations.
Comprehensive Manufacturing Cybersecurity Platform
Manufacturing organizations face unique cybersecurity challenges that require specialized expertise—connected production systems that create new attack vectors, legacy equipment with extended lifecycles that can't be easily updated, and the critical importance of maintaining continuous operations.
You need enterprise-level security expertise, but building that internally isn't practical for many manufacturers. Our platform gives you access to comprehensive security capabilities and the expertise to manage them effectively. From protecting corporate networks to isolating production systems, we deliver prevention, detection, response, and compliance management backed by 24/7 security expertise—all through one platform, one agent.
Why Manufacturers Need Specialized Cybersecurity
Manufacturing environments encompass complex interconnected systems spanning IT, operational technology, and IoT devices. This convergence creates unique challenges that require security solutions built to understand the realities of production environments where downtime directly impacts your bottom line and customer commitments.
Connected operations expand attack surface
Smart factories and connected industrial devices significantly expand your attack surface. Legacy operational technology systems now connect to corporate networks, creating new pathways for attackers to infiltrate production systems and cause disruption that can halt production lines.
Legacy systems create persistent vulnerabilities
Manufacturing organizations rely on operational technology with extended lifecycles—equipment that operates for 20+ years. These systems often run outdated software that cannot be easily patched, creating vulnerabilities that attackers specifically target because they know manufacturers require uptime to meet their contractual obligations.
Supply chain dependencies amplify risk exposure
Manufacturing operations depend on extensive supplier networks and third-party vendors who connect to production systems and access sensitive data. When these partners experience breaches, like supply chain attacks that impact numerous manufacturers, the cascade effect can disrupt global operations, halt production, and create downstream impacts that persist for months across entire industry sectors.
With the Todyl Platform, Manufacturing Organizations:
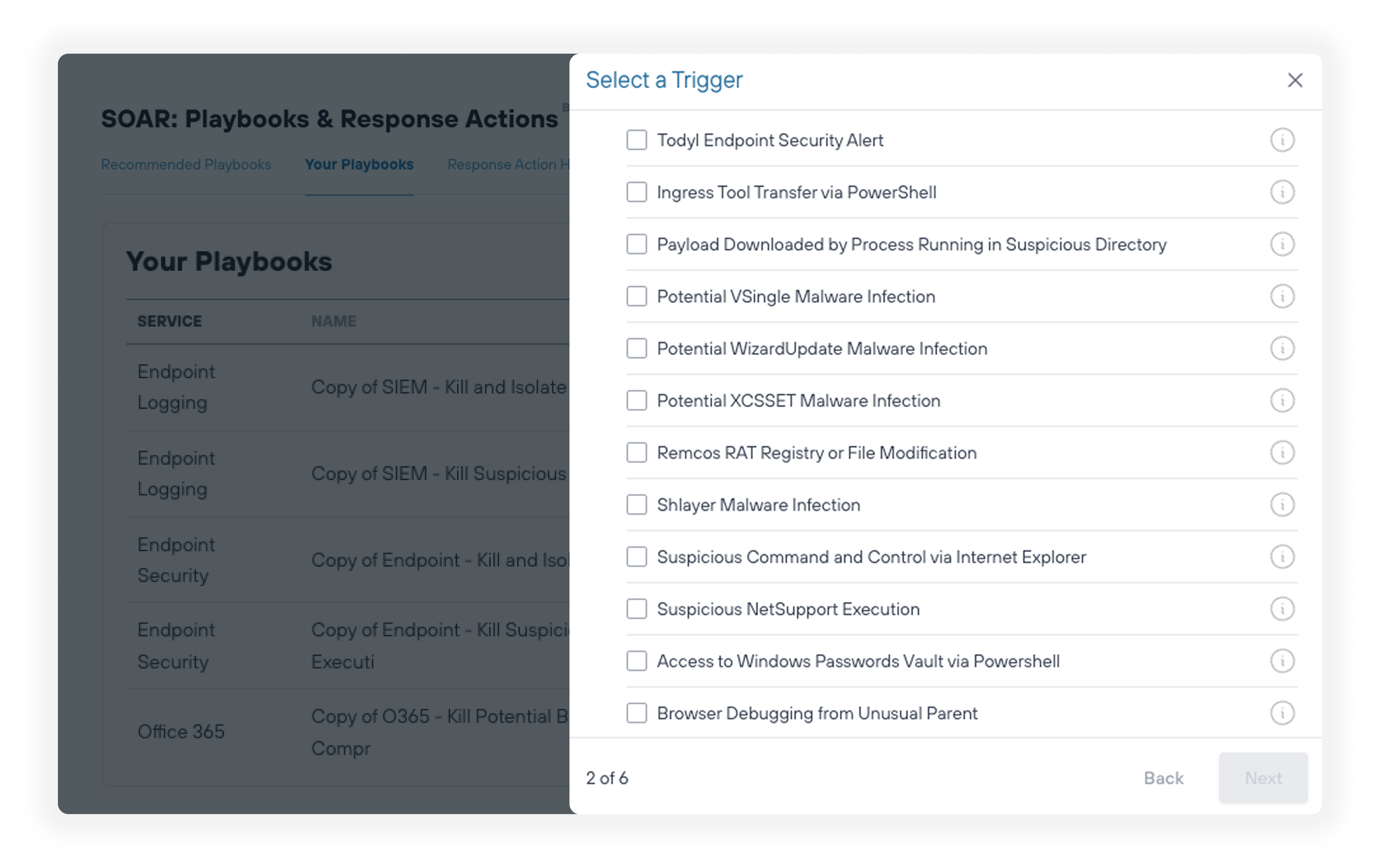
Ensure production uptime and on-time delivery
Maintain production uptime with security that doesn't interfere with critical operations. Our platform provides 24/7 monitoring and automated response capabilities that protect against threats while ensuring business continuity. We understand that production delays impact customer relationships and contract commitments.
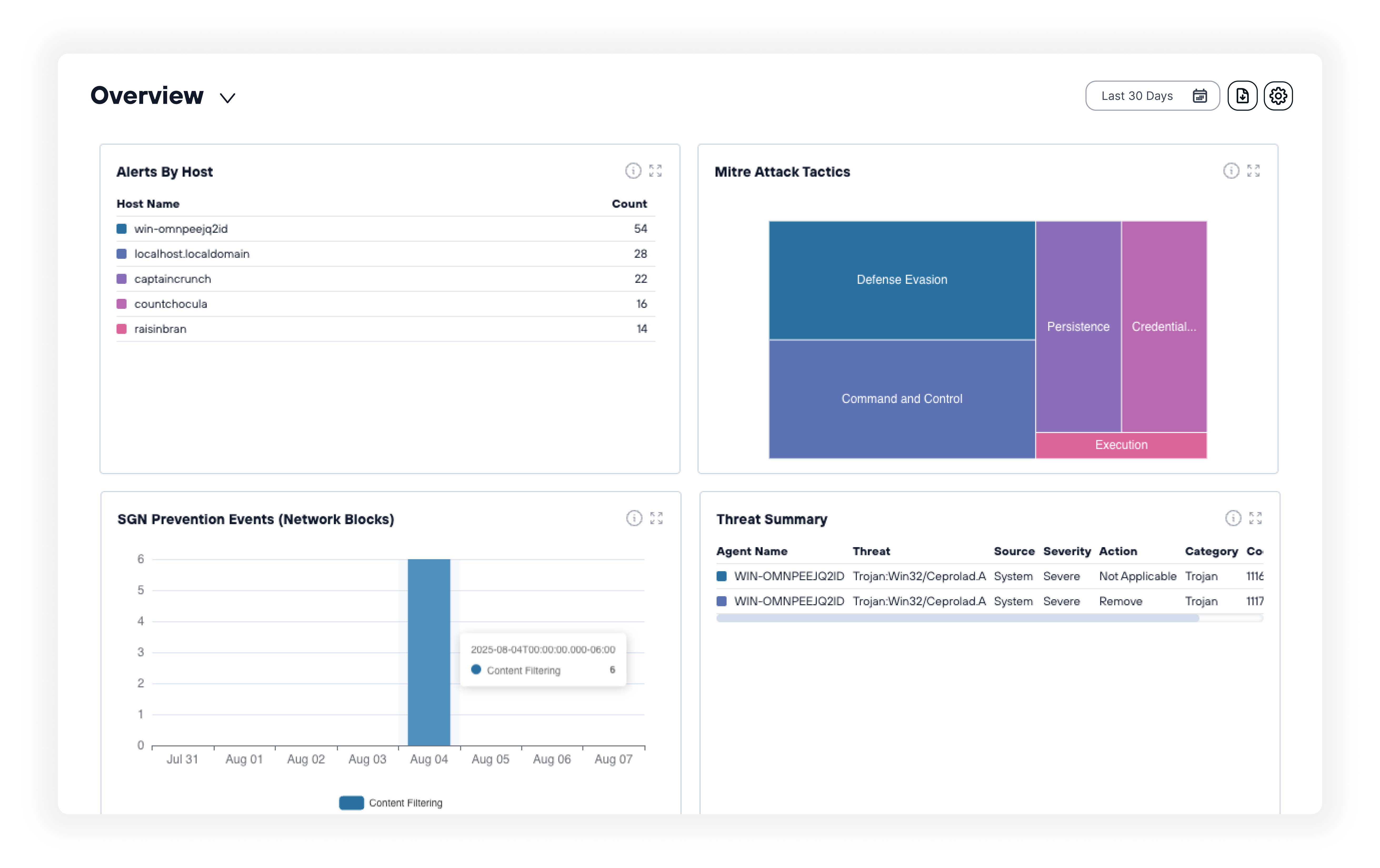
Protect intellectual property and trade secrets
Safeguard proprietary designs, processes, and manufacturing innovations from cybercriminals seeking to steal your competitive advantages. Our advanced threat detection identifies unusual data access patterns and helps prevent the theft of valuable intellectual property assets that differentiate you in your market.
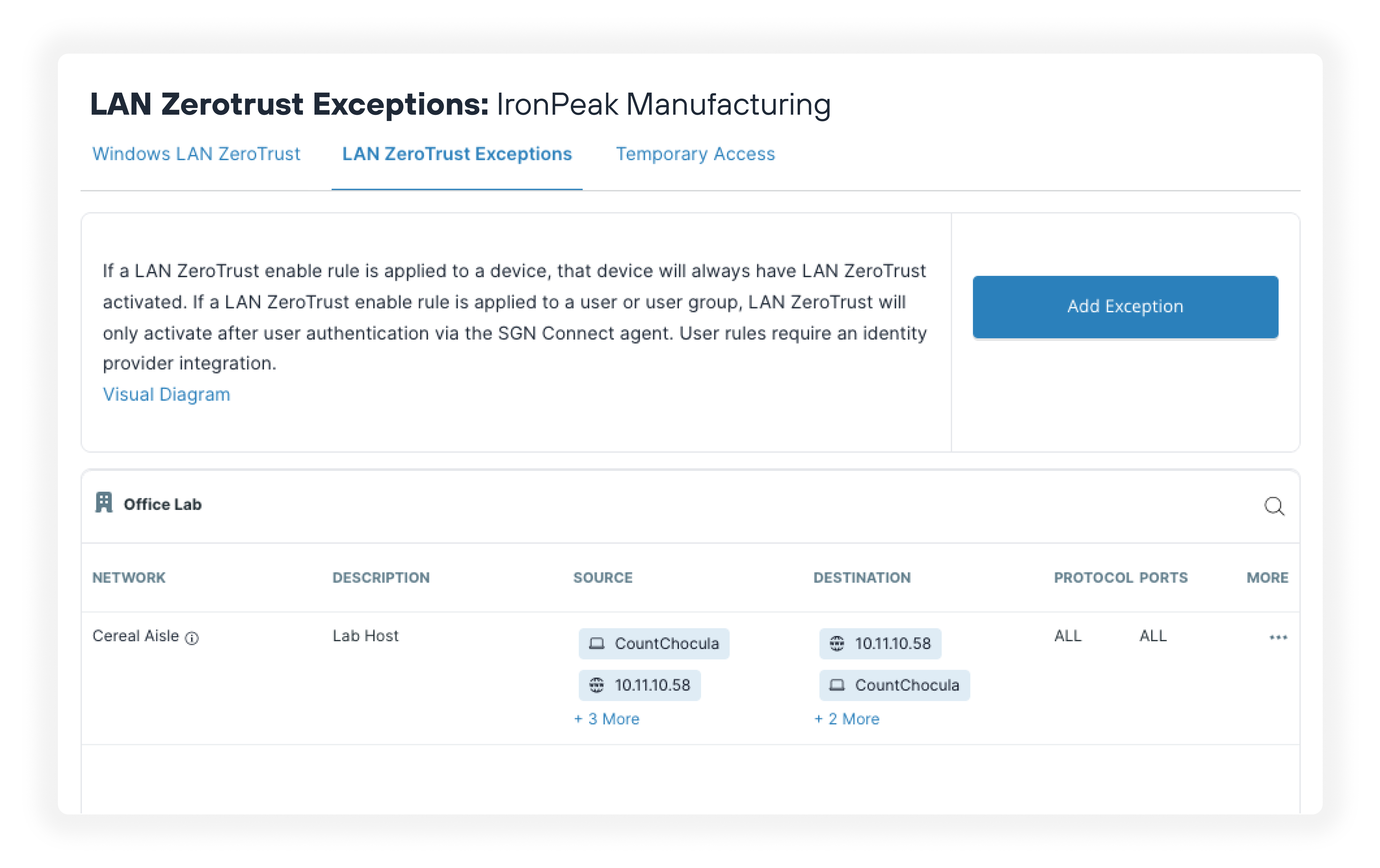
Manage third-party and supply chain risk
Protect your operations through network segmentation that isolates connected devices and role based access controls based on zero trust principles. Our platform helps you implement granular third-party access controls while keeping critical production systems separate from potential supply chain compromises that could disrupt your operations.
Partner with Manufacturing Cybersecurity Experts
Ready to strengthen your cybersecurity posture?
Get connected with a qualified partner in your area who can design a comprehensive security program tailored to your manufacturing operations and business requirements.
