The Söze Syndicate: Identifying a Major Threat Group and Exposing its Evolving Tactics Targeting SMBs
Business Email Compromise (BEC) continues to evolve into one of the most pervasive and damaging cyber threats in the modern digital landscape. As small and medium businesses enhance their defenses with endpoint security, attackers are adapting, seeking new ways to bypass these barriers. The shift in tactics is stark: rather than rely on traditional malware, threat actors are exploiting human error, trust, and communication channels, focused on services that remain vulnerable.
This threat has intensified as bad actors sharpen their tactics, becoming more sophisticated in their approach. Despite the rising danger, many organizations remain without Identity Threat Detection and Response (ITDR), leaving a critical gap in their defenses and creating a prime target for attackers. They exploit it with precision, using tactics like credential theft, adversary in the middle (AiTM), and session hijacking, continuously refining their tactics, techniques, and procedures (TTPs) to evade detection. MFA alone is no longer enough.
Throughout 2024, the Todyl MXDR team witnessed a staggering 558% surge in AiTM, account takeover (ATO), and BEC-related attacks. Most recently, they uncovered a suspicious access pattern originating from a small hosting provider targeting Microsoft 365 services.
The pattern revealed a failed login attempt, swiftly followed by a series of successful logins without any subsequent mailbox access or obvious malicious activity afterward. Threat actors often use this tactic to verify credentials and steal valid Microsoft 365 access tokens, which are later sold on underground marketplaces.
Starting with the rapid, likely automated login activity, we enabled a targeted threat hunt. This proactive approach enables us to continuously improve our detection capabilities, staying ahead in the ever shifting threat landscape
We began by analyzing Microsoft 365 and Azure logs, merging telemetry from both sources to gain a clearer picture of the threat actor’s behavior. Microsoft 365 telemetry alone provides limited insight, and Azure’s threat detection capabilities are also constrained. These blind spots make it challenging to correlate activity across platforms, especially as threat actors can pivot between hosted applications like SharePoint, Outlook for Web, and OneDrive.
Todyl MXDR conducts regular, targeted threat hunts tailored to each unique environment we support, providing actionable reporting to help proactively identify and mitigate potential security risks. By leveraging advanced analytics, threat intelligence, and in-depth knowledge of attack techniques, we can identify potential threats that automated tools might miss and uncover vulnerabilities. Using what we learn, we continuously improve our detection capabilities automatically for all organizations we support. Our proactive approach focuses on strengthening security postures, gaining comprehensive visibility, and accelerating response.
Business Email Compromise (BEC) continues to evolve into one of the most pervasive and damaging cyber threats in the modern digital landscape. As small and medium businesses enhance their defenses with endpoint security, attackers are adapting, seeking new ways to bypass these barriers. The shift in tactics is stark: rather than rely on traditional malware, threat actors are exploiting human error, trust, and communication channels, focused on services that remain vulnerable.
This threat has intensified as bad actors sharpen their tactics, becoming more sophisticated in their approach. Despite the rising danger, many organizations remain without Identity Threat Detection and Response (ITDR), leaving a critical gap in their defenses and creating a prime target for attackers. They exploit it with precision, using tactics like credential theft, adversary in the middle (AiTM), and session hijacking, continuously refining their tactics, techniques, and procedures (TTPs) to evade detection. MFA alone is no longer enough.
Throughout 2024, the Todyl MXDR team witnessed a staggering 558% surge in AiTM, account takeover (ATO), and BEC-related attacks. Most recently, they uncovered a suspicious access pattern originating from a small hosting provider targeting Microsoft 365 services.
The pattern revealed a failed login attempt, swiftly followed by a series of successful logins without any subsequent mailbox access or obvious malicious activity afterward. Threat actors often use this tactic to verify credentials and steal valid Microsoft 365 access tokens, which are later sold on underground marketplaces.
Starting with the rapid, likely automated login activity, we enabled a targeted threat hunt. This proactive approach enables us to continuously improve our detection capabilities, staying ahead in the ever shifting threat landscape
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Suspendisse varius enim in eros elementum tristique. Duis cursus, mi quis viverra ornare, eros dolor interdum nulla, ut commodo diam libero vitae erat. Aenean faucibus nibh et justo cursus id rutrum lorem imperdiet. Nunc ut sem vitae risus tristique posuere.
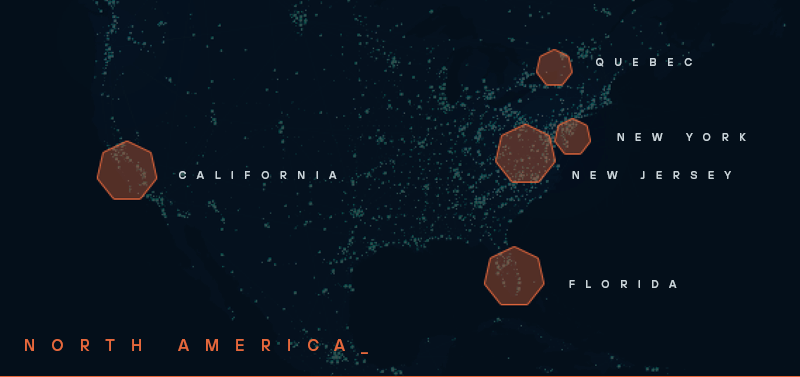
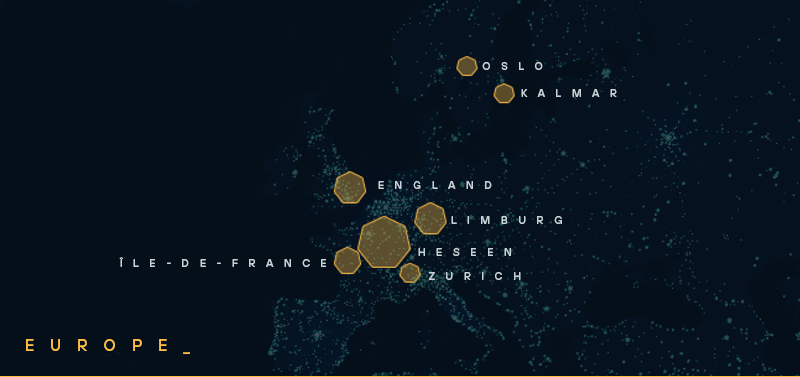
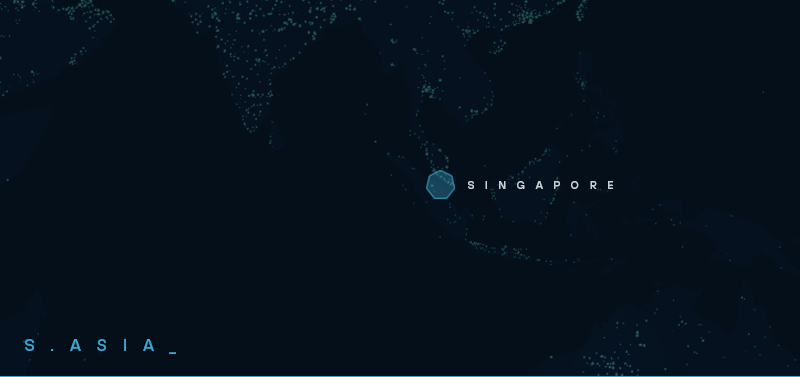
The sheer volume of hosts is staggering, and managing such a large fleet requires significant capital and automation, pointing to a well-funded and operationally mature group. They also leveraged trusted proxy services like Cloudflare to hide their phishing lures and malicious login pages, enabling them to bypass web security gateways and URL filters, further underscoring their advanced capabilities and sophistication.
The threat actor's infrastructure, along with the organizations they targeted, raised many questions and sparked conversation around their true objectives and capabilities:
In the remainder of this article, we break down the TTPs linked to this group and share three real-world stories that illustrate the challenges of detecting and responding to these sophisticated attacks.
TTPs Affiliated with the Söze Syndicate
The threat group infrastructure is incredibly active and has accelerated over the last 3 months. At the peak, approximately 65% of all attempted BEC cases across Todyl came from this group, with the vast majority being pre-infected and newly onboarded organizations. The attacks targeted everything from very small businesses to mid-market companies across legal, construction, critical infrastructure, defense, health care, non-profit, and many other industries.
The group exhibits high levels of patience with low and slow tactics, attempting to avoid detection while using advanced impersonation techniques to compromise accounts. Their TTPs are highly effective at bypassing multi-factor authentication, and use a variety of different strategies including:
Adversary in the Middle (AiTM)
SharePoint Phishing
Rogue Application Installation
After the initial compromise and theft of session tokens, they put significant effort into remaining stealthy, attempting to hide their activity by installing applications or logging indirectly from Microsoft using outlook.office.com or Azure.
The threat actors use different service providers for different purposes, including password spraying, scanning, and running as relays. They frequently pivot between the different host blocks, using one for initial compromise and another for ongoing monitoring of mailboxes. By doing so, they make it even more difficult to track.
It's important to note that this is an ongoing investigation. As such, we omitted IoCs from the article to ensure we can continue working with authorities.
Before diving into the three stories, here are steps every business should take to strengthen their security posture against these attacks.
Adversary in the Middle (AiTM)
Even though MFA can be bypassed by AiTM and other TTPs, it is still a critical line of defense that can slow attackers down.
Implement ITDR
With the focus on compromising identity, it’s imperative to have visibility and advanced correlation that can detect identity compromise with accuracy.
Optimize Your SIEM Configuration
The sophistication of these attacks requires a SIEM with properly configured Microsoft 365 and Azure ingestion.
Deploy Secure Access Service Edge (SASE)
SASE enables businesses to lock down their Office 365 and other applications to only be accessible from specific IP ranges and specific user identities, virtually eliminating the attack surface area.
Find the Right MDR Provider
Given the sophistication of BEC today, it's imperative to find an MDR provider with deep experience and capabilities with ITDR as well as Microsoft 365 and Azure/EntraID.
Three Real-World Stories of Impact
Building up such an extensive infrastructure takes time and resources that demand a significant return. The threat actors behind this are financially motivated, sophisticated, and leverage operational security practices to evade attribution and detection as evidenced by the following three stories.
Adversary in the Middle

Small non-profit
An individual supporting the non-profit’s operations with access to financials.
Compromise the target's Microsoft 365 identity to uncover potential opportunities for financial gain.
- SIEM
- SOAR
- MXDR
The business was pre-infected prior to deploying Todyl. The threat actor used very manual, low and slow tradecraft that was virtually indistinguishable from typical user activity.
- Microsoft 365
- Azure/EntraID
Upon ingesting just three days’ worth of Microsoft 365 and Azure data, our anomaly framework detected the attempted BEC.
Todyl SOAR automatically revoked access at the same time the alert triggered. We identified an attempt to change payment destinations for an invoice, sent an alert, and closely coordinated to prevent the transfer from occurring.
Phishing through SharePoint

Mid-size manufacturer
The attack began with executives in product development and supply chain—likely an opportunistic approach—and possibly indicative of purchased credentials. Both users were attacked on the same day within an hour.
Pivot more deeply into the organization, specifically targeting users related to finance or accounting. Infiltrate the target’s Microsoft 365 identity to identify opportunities for financial gain.
- Managed Cloud SIEM
Threat actors target internal infrastructure, such as SharePoint, for several reasons:sed credentials. Both users were attacked on the same day within an hour.
- The internal infrastructure is trusted and access to files/links may bypass perimeter security controls
- Users often instinctively trust content that’s posted internally, and focus their attention on external threats
- Users are accustomed to giving credentials to log into SharePoint when clicking on links in an email and may ignore other clues to a phishing site if the page looks like an official Microsoft login
- Microsoft 365
- Azure/EntraID
Todyl detected anomalous access and SharePoint file creation. The configuration was set to detect-only and neither SOAR or MXDR were enabled.
Despite not having MXDR enabled, we closely coordinated to ensure access was completely reset for all the affected users prior to any exfiltration.
Rogue Application Install

Small accounting firm
The initial foothold was an individual accountant
Pivot to other internal staff to intercept and modify payment instructions.
- Managed Cloud SIEM
If installation of the software is allowed, further login activity is not required. The user’s mailbox can be cloned, and further access to mail is allowed directly without login.
- Microsoft 365
Todyl triggered an immediate alert based on a rogue application ID. Further analysis showed the threat actor assembling a list of potential victims and creating emails for a spearphishing campaign to internal and external targets.
The business did not yet have our MXDR services or SOAR configuration in place, and were promptly notified via SIEM to take action and revoke the application.
The Critical Role of ITDR
Our investigation highlights the importance of having ITDR with ML-powered behavioral detections to identify and stop threats early. Most BEC and ITDR solutions depend on static, signature-based rules to detect activities like impossible travel and mail forwarding, which can be noisy, unreliable, and are often triggered well-after initial access.
Threat actors are aware of what triggers traditional detection rules for identity-based attacks and BEC. This makes it crucial to look for anomalies---instances where behavior deviates from a user’s expected activity---to identify threats that would otherwise go undetected.
At Todyl, our anomaly framework lives in Todyl Managed Cloud SIEM and is fully integrated with our SOAR module, resulting in earlier, high fidelity detections with minimal noise that can automatically shut down initial access. Our anomaly framework uses ML rules to correlate anomalies, linking seemingly unrelated activities together. By doing so, security teams can detect threats earlier while simultaneously improving true positive rates.
By leveraging this ML-powered anomaly framework, we address the deficiencies of static and signature-based detection techniques. This approach enables us to take a different approach to ITDR at Todyl, which is included in our MXDR offering, providing fewer false positives, faster detections, and improved security outcomes.
At Todyl, ITDR is included as part of our MXDR service. With threat actors focused on compromising digital identities, we believe no MDR service is complete without it. All organizations that use Todyl MXDR that ingest Office 365 and Azure logs receive 24x7 ITDR backed by our ML-powered anomaly framework.
